Cybersecurity Challenges in Education: Protecting Against Threats
Combating Phishing and Social Engineering Attacks
Understanding Phishing Tactics
Phishing attacks are a prevalent cybersecurity threat targeting educational institutions, often leveraging social engineering techniques to manipulate individuals into divulging sensitive information. These attacks can take various forms, from deceptive emails mimicking legitimate university communications to malicious websites designed to mimic familiar login portals. Understanding the common tactics used by phishers, such as spoofing, urgency, and personalization, is crucial for preventing successful attacks. Recognizing these patterns allows educators and students to critically evaluate emails, links, and requests before responding, safeguarding institutional data and individual accounts.
A key element in combating phishing is educating users about the red flags associated with suspicious communications. This includes scrutinizing sender addresses for inconsistencies, checking the legitimacy of website URLs, and avoiding clicking on unfamiliar or suspicious links. Educating staff and students about these crucial aspects of online safety is paramount to building a robust defense against phishing attempts. A well-informed community is far more resilient to these types of attacks, reducing the risk of sensitive data breaches and maintaining the integrity of the educational environment.
Implementing Robust Security Measures
Beyond user education, robust security measures are essential to deter phishing and social engineering attacks. This includes implementing multi-factor authentication (MFA) for all critical accounts, which adds an extra layer of security by requiring verification beyond a simple password. Regular software updates and security patches are crucial to address vulnerabilities that attackers might exploit. Strong passwords, with a minimum length and complexity, are also vital for securing accounts against unauthorized access. These measures are fundamental to creating a secure environment, minimizing the impact of potential breaches, and safeguarding sensitive data.
Implementing email filtering systems and intrusion detection systems further enhances the security posture. These systems can identify and block suspicious emails, preventing them from reaching inboxes, and detect unusual network activities, which could signal a potential attack. Regular security audits and penetration testing help assess the effectiveness of existing security measures, identifying potential weaknesses and improving overall security protocols. These proactive steps significantly reduce the risk of successful attacks and protect the institution's valuable resources.
Encouraging a Culture of Security Awareness
Establishing a culture of security awareness within the educational community is vital for long-term protection against phishing and social engineering attacks. Regular security training sessions for staff and students can equip them with the knowledge and skills needed to identify and report suspicious activities. Promoting open communication channels, where individuals feel comfortable reporting potential threats, fosters a proactive security environment. This includes establishing clear procedures for reporting suspicious emails, websites, or other online communications.
Encouraging the reporting of suspicious activity is crucial for maintaining a strong defense. A culture of security awareness empowers individuals to be vigilant and take proactive steps to protect themselves and the institution. By fostering a sense of shared responsibility and encouraging open communication, educational institutions can create a more secure environment for everyone, effectively combating the ever-evolving threats of phishing and social engineering.
Strengthening Network Security and Infrastructure
Improving Network Security Measures
Robust network security is paramount in educational institutions, safeguarding sensitive student data, faculty research, and institutional resources. Implementing multi-layered security protocols, including firewalls, intrusion detection systems, and antivirus software, is crucial. Regular security audits and vulnerability assessments are essential to identify and address potential weaknesses before they can be exploited. This proactive approach helps prevent unauthorized access, data breaches, and disruptions to essential educational services, contributing to a secure and reliable learning environment.
Furthermore, educating students and staff about cybersecurity best practices is vital. Training programs should cover topics such as recognizing phishing attempts, strong password creation, safe online browsing habits, and reporting suspicious activity. Empowering users with the knowledge and skills to protect themselves and the network is a critical component of a comprehensive security strategy. This preventative measure greatly reduces the risk of human error contributing to security breaches.
Fortifying Infrastructure and Maintaining Resilience
Ensuring the physical security of network infrastructure is equally important. Protecting server rooms, network equipment, and other critical infrastructure from physical threats, such as theft, vandalism, or natural disasters, is crucial. Implementing robust backup and disaster recovery plans is essential to minimize downtime and data loss in case of an incident. This includes regularly backing up critical data and having a clear plan for restoring systems and services in the event of a disruption. This proactive approach helps maintain the continuity of educational operations.
Maintaining updated and reliable hardware and software is also a key component of infrastructure security. Regularly updating operating systems, applications, and security software patches is vital to mitigate known vulnerabilities. Investing in robust infrastructure, including redundant systems and secure data centers, enhances the institution's resilience against various cyber threats. This ensures the reliable delivery of services, protects sensitive data, and helps educational institutions operate smoothly during unexpected events.
Regularly reviewing and updating policies and procedures is equally important. This includes establishing clear guidelines for data handling, access control, and incident response. Policies must be regularly reviewed and updated to reflect the evolving cyber threat landscape and best practices. This ensures that the institution remains compliant with relevant regulations and effectively addresses emerging security challenges. This preventative measure is vital to maintaining a strong posture against evolving threats.
Implementing robust network segmentation and access controls is also important. Restricting access to sensitive data and resources to authorized users is crucial. This can be achieved through network segmentation, which isolates different parts of the network, and access control lists, which define who has permission to access specific resources. This layered approach helps to limit the impact of a security breach and ensures that only authorized personnel have access to sensitive information.
Implementing Multi-Factor Authentication and Access Control
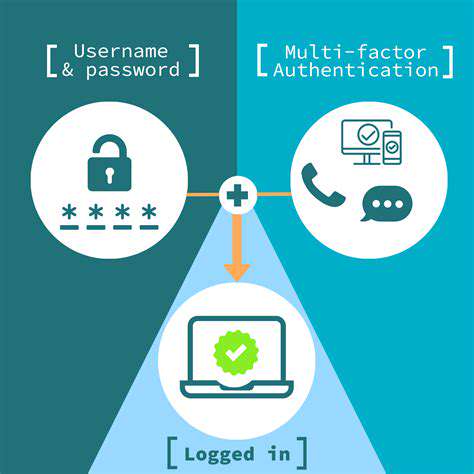
Understanding Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) is a security process that requires users to provide multiple forms of identification to verify their identity before accessing a resource. This adds an extra layer of security, making it significantly harder for unauthorized individuals to gain access, even if they have obtained one form of authentication, such as a password.
By requiring more than just a username and password, MFA strengthens the overall security posture of any system. This is crucial in today's digital landscape, where cyber threats are constantly evolving and becoming more sophisticated. MFA enhances the protection of sensitive data and critical systems from unauthorized access.
Types of MFA Factors
Various authentication factors are used in MFA systems. These include something you know (like a password or PIN), something you have (like a security token or smartphone), and something you are (like biometric data such as fingerprints or facial recognition). Choosing the right combination of factors is vital to create a strong and effective security measure.
Each factor has its own strengths and weaknesses. For example, something you know, like a password, can be easily compromised if not managed securely. Something you have, like a security token, offers a stronger barrier against unauthorized access, but can be lost or stolen.
Implementing MFA in Different Systems
Implementing MFA can be tailored to specific systems and applications. This may involve configuring various authentication methods, such as integrating with existing security providers or developing custom solutions to meet specific security needs. Careful consideration of the system architecture and user experience is crucial for a successful implementation.
Different platforms and applications will have different requirements for MFA implementation. Careful planning and testing are critical to ensure a smooth transition and avoid disruptions to normal operations.
Benefits of Implementing MFA
Implementing MFA provides a significant boost to security. It drastically reduces the risk of unauthorized access to sensitive data and systems, which is essential in today's increasingly complex digital environment. This significantly enhances the overall security posture of any organization.
Beyond enhanced security, MFA also often improves user trust and confidence in online systems. Users feel more secure knowing their accounts are protected by multiple layers of verification.
User Experience and Adoption
When implementing MFA, it's essential to consider the user experience. A seamless and user-friendly MFA process will encourage adoption and minimize frustration. This includes clear instructions and intuitive interfaces to guide users through the authentication process.
A poorly designed MFA system can lead to user resistance and decreased adoption. User training and support are critical components to ensure a successful and positive user experience. Thorough documentation and readily available support channels can minimize user confusion and encourage compliance with the new security measures.
Security Considerations and Best Practices
Security considerations extend beyond the choice of authentication factors. Robust password policies, secure storage of secrets, and regular security audits are crucial for a comprehensive MFA strategy. Security best practices need to be integrated into the overall security framework of an organization.
Regular security assessments and penetration testing are also essential to identify and mitigate potential vulnerabilities in the MFA implementation. Staying informed about the latest security threats and adapting to evolving security needs is crucial for maintaining a strong security posture.
Read more about Cybersecurity Challenges in Education: Protecting Against Threats
Hot Recommendations
- The Gamified Parent Teacher Conference: Engaging Stakeholders
- Gamification in Education: Making Learning Irresistibly Fun
- The Future of School Libraries: AI for Personalized Recommendations
- EdTech and the Future of Creative Industries
- Empowering Student Choice: The Core of Personalized Learning
- Building Community in a Hybrid Learning Setting
- VR for Special Education: Tailored Immersive Experiences
- Measuring the True Value of EdTech: Beyond Adoption Rates
- Addressing Digital Divide in AI Educational Access
- Preparing the Workforce for AI Integration in Their Careers