Ensuring Data Security in Mobile Learning Solutions
The Evolving Threat Landscape in Mobile Learning
Mobile Learning App Security Vulnerabilities
While mobile learning apps provide convenient access to educational materials, they often harbor security flaws that jeopardize sensitive user information. These weaknesses may arise from multiple factors, including subpar encryption methods, insufficient authentication processes, and the risk of harmful code insertions. Recognizing these vulnerabilities proves essential for both developers and users to reduce risks and maintain a protected learning space.
Additionally, the growing dependence on cloud storage for mobile learning resources makes these apps susceptible to potential cloud security breaches. Safeguarding cloud-stored data—whether student records, course content, or payment details—demands rigorous security protocols from both app creators and cloud service providers.
The Rise of Phishing and Malware Attacks
Phishing threats don't spare mobile learning platforms. Cybercriminals craft fake apps that imitate genuine learning services, duping users into surrendering login credentials or installing malware. This highlights the critical need to verify app origins and exercise vigilance when downloading apps or accessing unfamiliar links.
Malware, including ransomware and spyware, can penetrate mobile devices through compromised apps or malicious files. Such attacks can interrupt learning, pilfer confidential data, and even encrypt information for ransom, necessitating costly recovery efforts.
Data Encryption and Privacy Concerns
Implementing strong data encryption remains vital for protecting sensitive information within mobile learning platforms. This involves encrypting user data both during storage and transmission to block unauthorized access. Neglecting robust encryption creates substantial security gaps that could lead to data leaks and privacy violations.
User Authentication and Access Control
Adopting stringent authentication measures, like multi-factor authentication (MFA), proves indispensable for preventing unauthorized entry into mobile learning accounts. This multi-step verification approach substantially bolsters security by demanding several confirmation steps, complicating attackers' efforts to access sensitive data.
The Role of Mobile Device Management (MDM)
Mobile Device Management (MDM) serves a pivotal function in securing devices used for mobile learning. MDM tools enable administrators to oversee device settings, enforce security rules, and distribute updates to keep devices shielded against emerging threats. These solutions also aid in preventing data loss by allowing remote data erasure on misplaced or stolen devices.
The Importance of Regular Security Audits and Updates
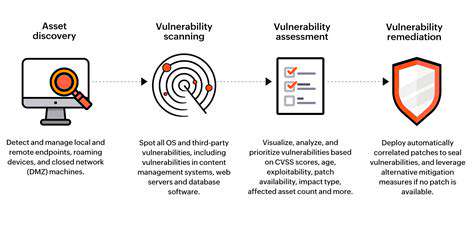
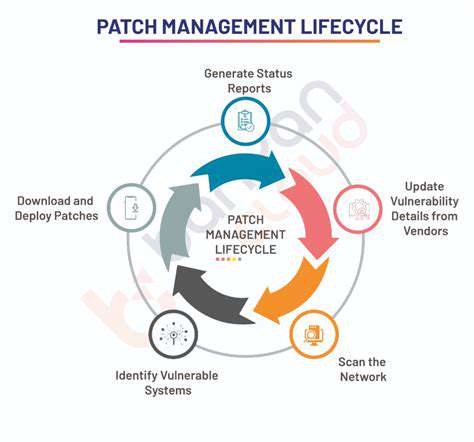
Conducting frequent security assessments of mobile learning applications remains crucial for detecting and rectifying potential weaknesses. These evaluations should examine the app's code integrity, data storage practices, and communication security. Moreover, promptly applying the latest security patches proves essential for countering new threats. Proactive security measures and constant vigilance help prevent breaches and preserve a secure learning environment.
Addressing the Need for User Education and Awareness
Educating users about mobile learning security holds equal importance. Users should understand the dangers of downloading apps from unverified sources, clicking questionable links, and sharing personal details. Equipping users with knowledge and security best practices strengthens the overall defense of the mobile learning ecosystem.
Implementing Robust Encryption Techniques
Understanding the Importance of Encryption
Strong encryption stands as a cornerstone for protecting sensitive data in mobile learning contexts. Given their portable nature, mobile devices frequently encounter security threats like unauthorized access, data leaks, and malicious intrusions. Deploying rigorous encryption protocols becomes imperative to shield user information, ensure privacy, and uphold the learning process's integrity. Without proper encryption, critical data—including student records, assessments, and financial information—could become exposed, with serious consequences for individuals and institutions.
Types of Encryption Algorithms
Diverse encryption algorithms exist, each with distinct advantages and limitations. Symmetric-key algorithms, such as AES (Advanced Encryption Standard), employ identical keys for encryption and decryption, offering faster processing. Asymmetric algorithms like RSA (Rivest-Shamir-Adleman) use separate keys for these functions, providing enhanced security through key exchange mechanisms. Selecting the right algorithm depends on data sensitivity, performance needs, and implementation complexity.
Key Management Best Practices
Effective key management remains fundamental for maintaining encrypted data security. Secure key generation, storage, and distribution protocols must be established. Keys should reside in protected environments, preferably within hardware security modules (HSMs) to prevent unauthorized retrieval. Regular key rotation and secure exchange methods help avert vulnerabilities and sustain encryption integrity. Meticulous key management planning minimizes compromise risks.
Implementing Encryption in Mobile Applications
Incorporating encryption into mobile apps demands careful evaluation of the application's structure and data pathways. Data requires encryption during storage and transmission to prevent unauthorized interception. Developers should utilize reputable encryption libraries and APIs to guarantee secure implementation aligned with industry standards. Different data types and sensitivity levels necessitate appropriate encryption methods, ensuring sensitive information remains protected from input through storage or transfer.
Data Encryption at Rest
Encrypting stored data safeguards information on mobile devices or cloud servers. This includes student records, course materials, and other confidential content. Encryption at rest involves converting data into unreadable formats using algorithms, ensuring protection even if storage systems are breached. Proper configuration of encryption tools proves vital for effective data-at-rest security.
Data Encryption in Transit
Encrypting data during transmission protects information moving between devices and servers. Secure protocols like TLS (Transport Layer Security) become indispensable for shielding communication channels. These protocols encrypt transmitted data, preventing interception and guaranteeing confidentiality. Secure network connections prove essential for thwarting man-in-the-middle attacks and other transmission threats.
Security Auditing and Regular Updates
Periodic security audits and updates ensure encryption strategies remain effective. Audits uncover vulnerabilities in encryption implementations. Prompt updates to encryption protocols and software address newly discovered threats. Security training for developers and users also forms a critical element of mobile learning security, ensuring proper encryption understanding and usage.
Multi-Factor Authentication (MFA) and Access Control
Implementing Multi-Factor Authentication
Multi-Factor Authentication (MFA) serves as a vital element of modern access control systems. It dramatically improves security by mandating multiple verification forms, substantially raising the difficulty for unauthorized parties to access sensitive systems. This layered defense surpasses basic username-password combinations, which frequently fall prey to phishing and brute-force attacks. Successful MFA implementation requires assessing organizational needs, risk thresholds, and technical capacities.
Selecting appropriate MFA methods proves critical. Options span from time-based one-time passwords (TOTP) via mobile apps to physical security keys. Choices should balance user convenience, security robustness, and system compatibility. Organizations must also prioritize MFA infrastructure security, ensuring resilience against potential attacks and maintaining authentication reliability.
Regular MFA policy reviews and updates remain essential. With cyber threats constantly evolving, proactive security measures become necessary. This includes monitoring new vulnerabilities and adjusting policies accordingly. User education about MFA importance and proper usage also ensures compliance and reduces errors.
Defining and Enforcing Access Control Policies
Comprehensive access control policies form the foundation of data protection. These regulations determine data accessibility parameters for different personnel. Clearly outlined roles and responsibilities, paired with detailed permission settings, restrict potential damage from unauthorized access. This encompasses establishing specific access tiers, limiting sensitive data availability to essential personnel, and implementing strict account management procedures.
Effective access control extends beyond policy creation to consistent monitoring and enforcement. Routine access privilege audits identify potential weaknesses and verify policy adherence. These reviews also detect abnormal access patterns indicating malicious activity or mistakes.
Stringent access control policies, reinforced by regular oversight, prove instrumental in preventing unauthorized data access. They also create accountability frameworks, facilitating quicker incident identification and response.
Read more about Ensuring Data Security in Mobile Learning Solutions
Hot Recommendations
- The Gamified Parent Teacher Conference: Engaging Stakeholders
- Gamification in Education: Making Learning Irresistibly Fun
- The Future of School Libraries: AI for Personalized Recommendations
- EdTech and the Future of Creative Industries
- Empowering Student Choice: The Core of Personalized Learning
- Building Community in a Hybrid Learning Setting
- VR for Special Education: Tailored Immersive Experiences
- Measuring the True Value of EdTech: Beyond Adoption Rates
- Addressing Digital Divide in AI Educational Access
- Preparing the Workforce for AI Integration in Their Careers